This is the multi-page printable view of this section.
Click here to print.
Return to the regular view of this page.
Getting Started
Warning
This documentation if for Ohlala Operations for Amazon EC2 beta.
This version is not suitable for production environments.
Note: The beta is currently available only in the us-east-1 and eu-west-1 AWS regions.
Before deploying Ohlala Operations for Amazon EC2, ensure you have the following:
- An AWS account that has been granted access to the beta AMI.
- One or more Windows EC2 instances to manage.
- AWS Systems Manager Agent (SSM Agent) installed and running on your instances (recommended for remote execution).
Request Access
To participate in the beta program, request access by emailing contact@ohlala.cloud with your AWS account ID. Once approved, you will receive details on how to launch the AMI.
Deployment Options
You can deploy Ohlala Operations for Amazon EC2 using one of the following methods:
This is documented in the following section: Terraform Deployment
This is documented in the following section: Cloudformation Deployment
First Steps
- Access the Web Interface: Open the ALB public URL in your browser provided as output of Terraform or CLoudformation.
- View Your Windows EC2 Instances: The system automatically detects and lists your instances.
- Run Your First Task: Test automation by executing a simple task like retrieving system logs.
Troubleshooting
If you encounter issues:
- Ensure your AWS account has been granted access to the AMI.
- Verify that your EC2 instances have the correct IAM roles.
- Check that AWS Systems Manager Agent is installed and running.
- Review logs for any error messages.
Next Steps
Deploy the solution either using CloudFormation Deployment or Terraform deployment.
Explore the full capabilities of Ohlala Operations for Amazon EC2 by setting up automation workflows and optimizing your Windows EC2 management.
For assistance, contact contact@ohlala.cloud.
Feel free to send any feedback you may have on this feedback form.
✨ Ohlala Operations - Automate Windows Server Management on AWS! ✨
1 - Prerequisites
You will need an AWS Account and sufficient IAM permissions to deploy the CloudFormation template or the terraform stack.
A VPC is required with at least two public subnets. See the Architecture page for more details.
Ohlala Automation for Amazon EC2 requires access to AWS Systems Manager service either through internet using an Internet Gateway or a VPC endpoint AWS Documentation.
An EC2 key pair is required.
You’ll also probably need a couple of Windows Server EC2 to test the features from the beta version. You need the AWS SSM agent installed on those EC2.
2 - SSM agent
Make sure the SSM agent is installed
Warning
This documentation if for Ohlala Operations for Amazon EC2 beta.
This version is not suitable for production environments.
Ohlala Operations for Amazon EC2 relies on the AWS Systems Manager (SSM) Agent to manage Windows EC2 instances effectively. The SSM Agent enables Systems Manager to update, manage, and configure these resources.
Inclusion in AWS AMIs
The SSM Agent is preinstalled on several Amazon Machine Images (AMIs) provided by AWS. Notably, it is included in:
- Windows Server 2012 R2: AMIs published in November 2016 or later.
- Windows Server 2016, 2019, 2022, and 2025: All standard versions (excluding Nano versions).
For a comprehensive list of AMIs with the SSM Agent preinstalled, refer to the AWS documentation.
Network Prerequisites
To ensure proper communication between the SSM Agent and AWS Systems Manager, consider the following network requirements:
-
Outbound Internet Access: The SSM Agent requires outbound access to the internet to communicate with the Systems Manager service. If your instances do not have direct internet access, you can set up VPC endpoints to facilitate this communication.
-
Instance Metadata Service (IMDS): The SSM Agent utilizes the Instance Metadata Service. Ensure that your instances can access the IPv4 address 169.254.169.254. Both IMDSv1 and IMDSv2 are supported.
-
No Inbound Ports Required: The SSM Agent initiates all communication with the Systems Manager service; therefore, no inbound ports need to be opened in your instance’s security group for Systems Manager functionality.
For detailed technical information about the SSM Agent, including installation and configuration guidance, visit the AWS Systems Manager User Guide.
IAM Instance Profiles
Typically, managing EC2 instances with AWS Systems Manager requires attaching an IAM instance profile to each instance to grant necessary permissions. However, Ohlala Operations for Amazon EC2 simplifies this process by configuring the Default Host Management Configuration (DHMC) by default. This approach eliminates the need for manual instance profile assignment, ensuring that Systems Manager has the required permissions to manage all instances in your AWS account and region. For more information, refer to the AWS documentation on DHMC.
For detailed technical information about the SSM Agent, including installation and configuration guidance, visit the AWS Systems Manager User Guide.
Default Host Management Configuration (DHMC)
Please note that AWS Systems Manager DHMC requires SSM Agent version > 3.2.582.0.
This is not mandatory but will ease configuration of your EC2 instances.
✨ Ohlala Operations - Automate Windows Server Management on AWS! ✨
3 - Cloudformation deployment
Prerequisites
Before deploying Ohlala Operations for Amazon EC2, you will need:
- An existing key pair
- A VPC with at least two subnets to deploy the Elastic Load balancer. You will need to have access to these network to access Ohlala Operations for Amazon EC2
Our cloudformation template is available at: cloudformation-stack.
Either use git to clone the repository or download it from the gitlab interface.
Deploy Ohlala Operations for Amazon EC2 to your AWS account
Open your AWS console and navigate to the Cloudformation console. Make sure you’re logged in to the correct AWS account and using the correct region.
Click Create stack.
Selecting the template
Select Choose an existing template and Upload a template file.
Choose the cloudformation template.yaml file provided on the gitlab repository.
Click Next.
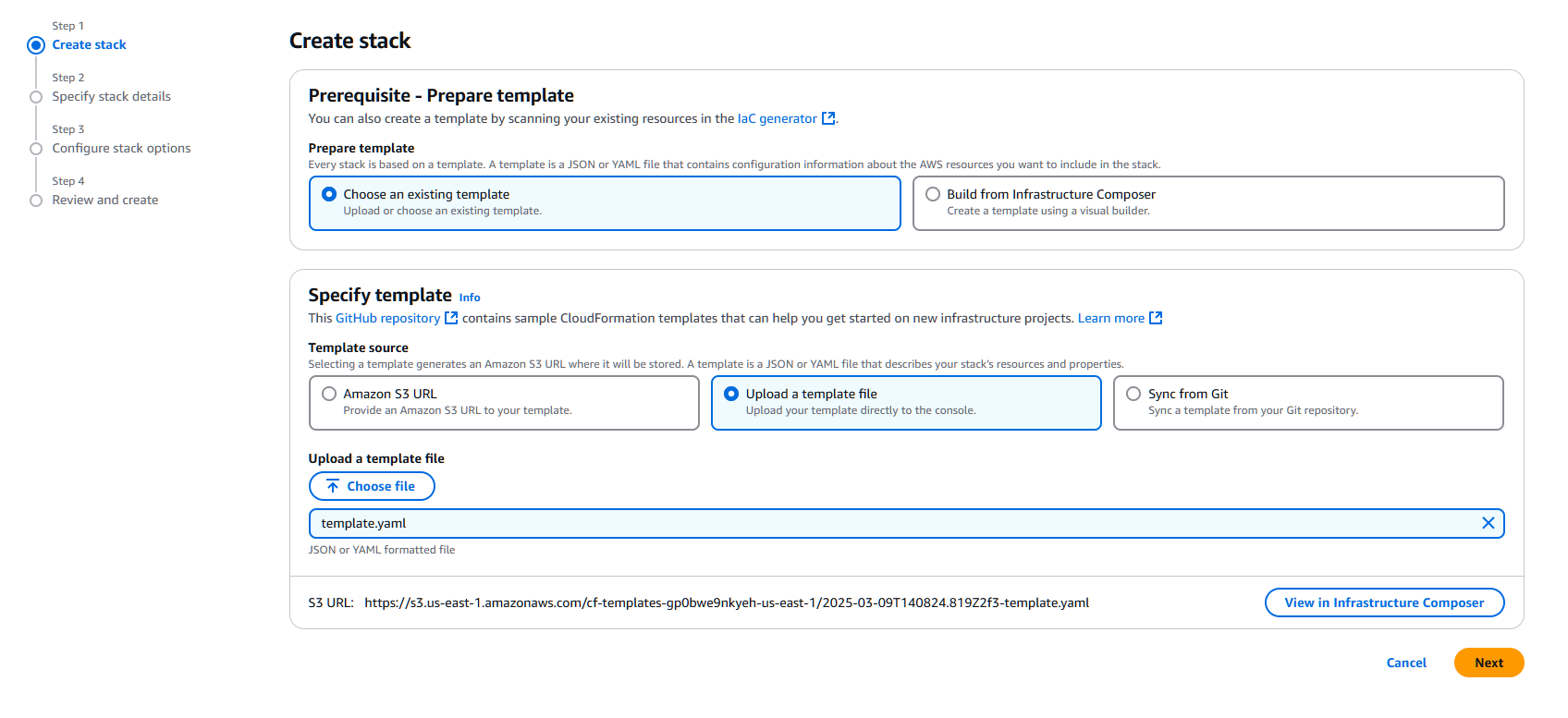
Stack parameters
Give a name to your stack deployment.
Select an instance type. For small to medium size (i.e. most deployment), t3.medium is recommended.
Select an existing EC2 key pair (this is mandatory for AWS marketplace products).
Select your VPC from the drop down menu.
Enter the CIDR allowed to connect to the public ALB of Ohlala Operations for Amazon EC2. Please be vigilant and enter a limited range.
We suggest having a look at your public IP address on https://api.ipify.org.
The default mask for one IP address is /32 as per the screenshot.
Finally, enter two different subnets from the drop down menus.
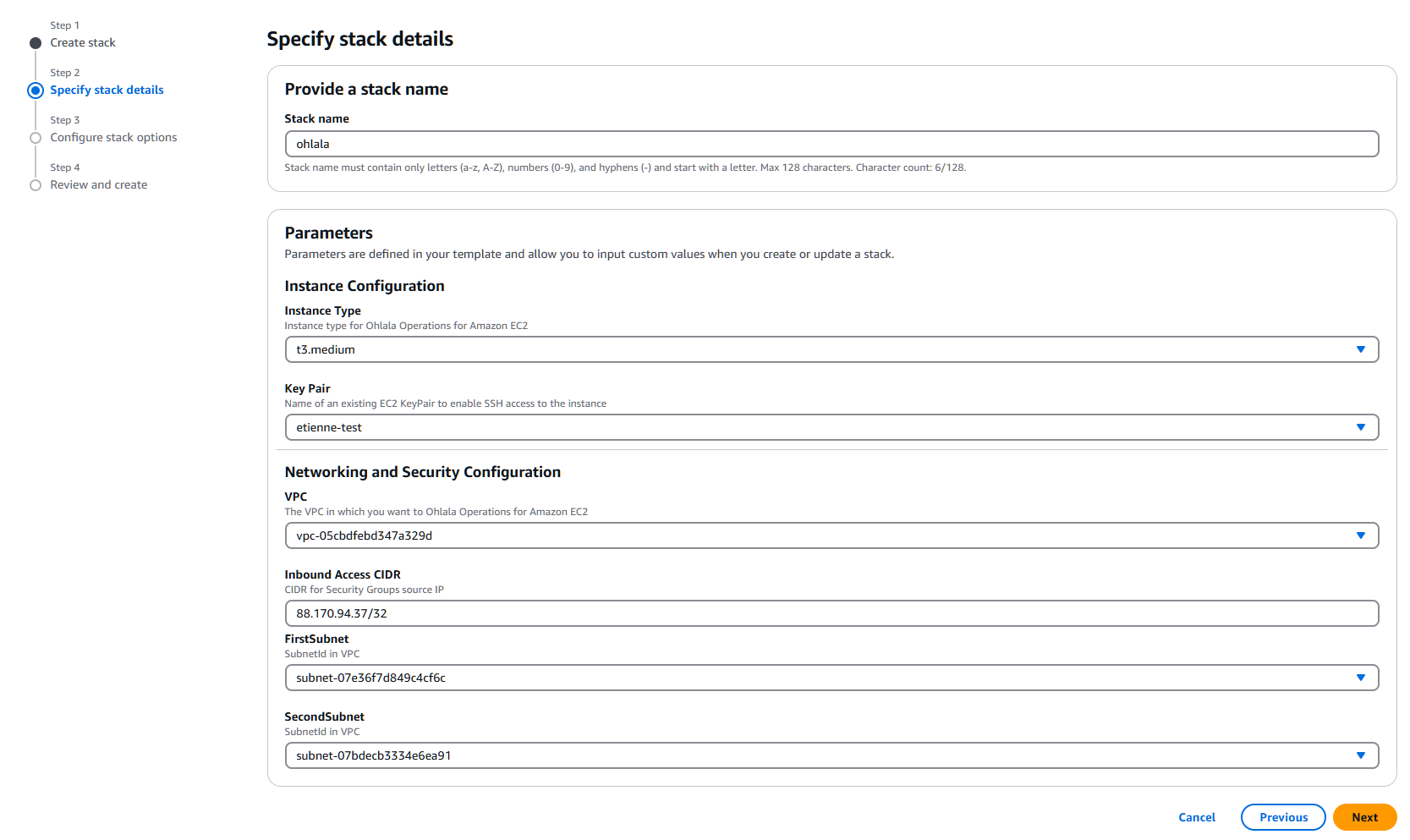
Additional parameters
Feel free to review the next page to comply with your company deployment policy.
Tick the box at the bottom of the page to acknowledge the deployment of IAM roles and policies.
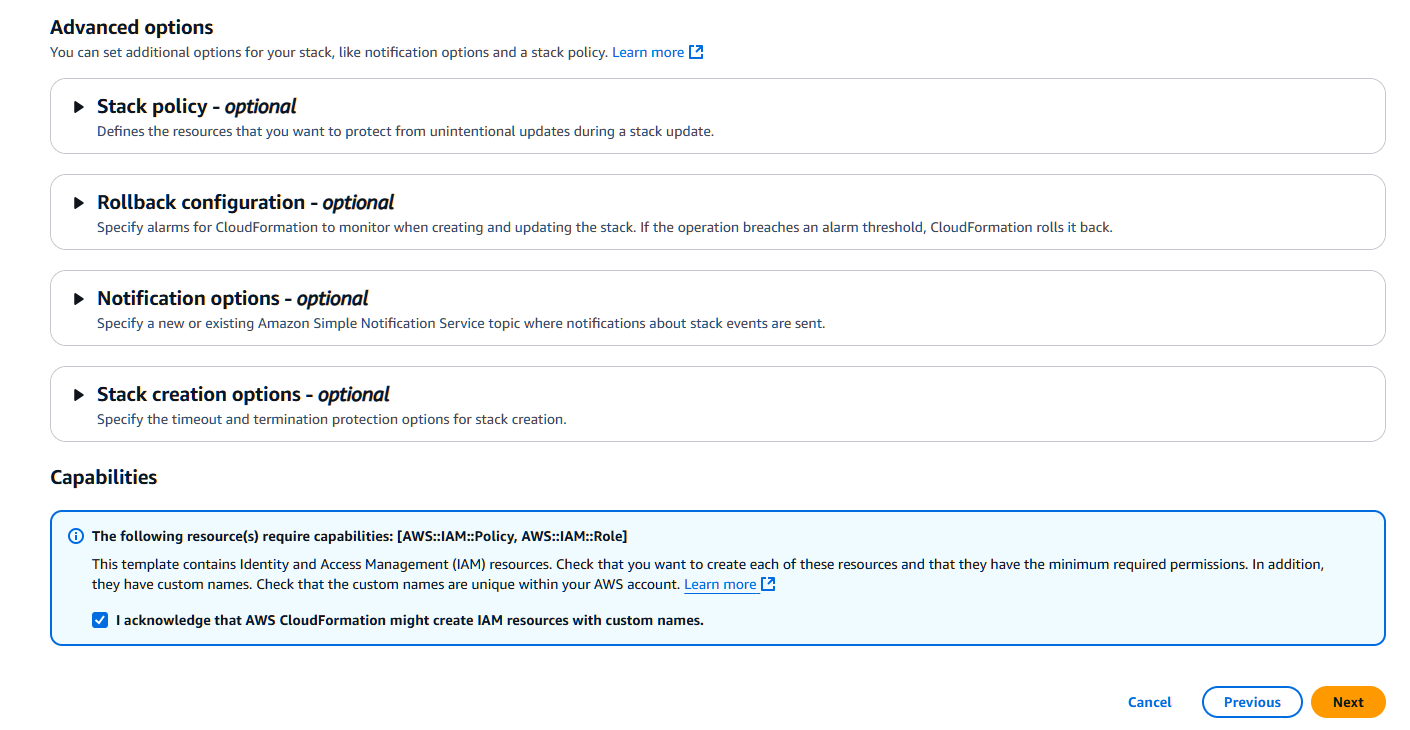
Final review
Review all the settings and click Submit.
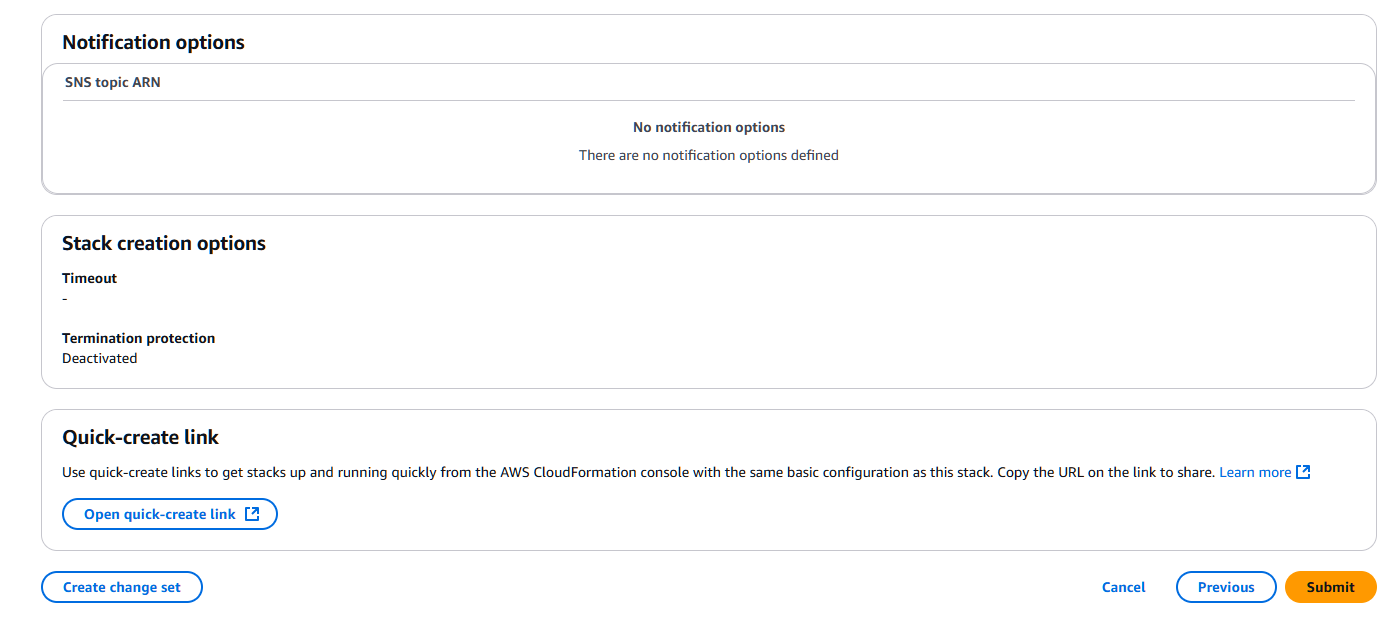
Follow-up
You can monitor the status of your stack in the cloudformation console.
It should finally show a status of CREATE_COMPLETE.
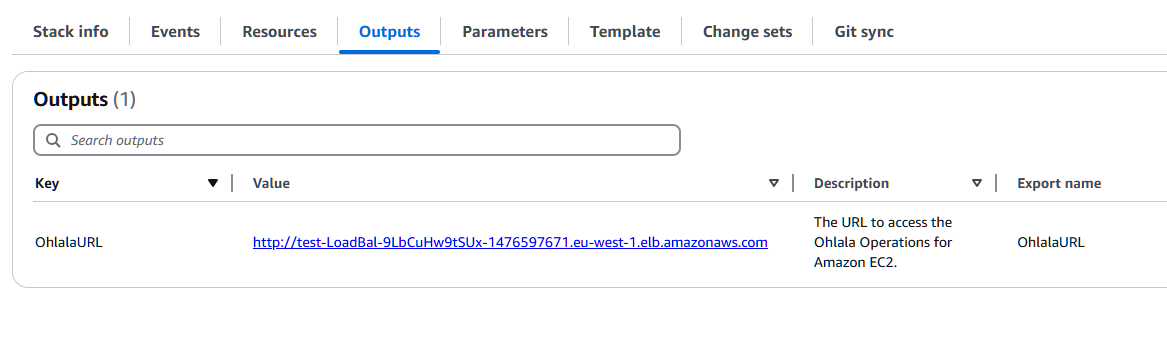
Output
The cloudformation stack provides the URL of your load balancer in the Outputs tab. Go ahead an open this link in a new tab (please allow a few minutes for the web interface to start up).
✨ Ohlala Operations - Automate Windows Server Management on AWS! ✨
4 - Terraform deployment
Our terraform stack is available at https://gitlab.com/ohlala-automation-solutions-public/beta/terraform-stack or you can directly download the zip file.
Clone the repository locally.
Instructions
Please have a look through the readme or the code of the repository. You will see what resources are deployed and what parameters are needed.
You can download terraform from their website.
Deployment
Open your favorite shell and navigate to the root folder of the repository.
Initialize the repository:
The output should look something like this:
Initializing the backend...
Initializing provider plugins...
- Reusing previous version of hashicorp/aws from the dependency lock file
- Reusing previous version of hashicorp/random from the dependency lock file
- Using previously-installed hashicorp/aws v5.91.0
- Using previously-installed hashicorp/random v3.7.1
Terraform has been successfully initialized!
You may now begin working with Terraform. Try running "terraform plan" to see
any changes that are required for your infrastructure. All Terraform commands
should now work.
If you ever set or change modules or backend configuration for Terraform,
rerun this command to reinitialize your working directory. If you forget, other
commands will detect it and remind you to do so if necessary.
View planned changes:
The output should look something like this:
...
Plan: 56 to add, 0 to change, 0 to destroy.
Changes to Outputs:
+ ohlala_url = (known after apply)
Note: You didn't use the -out option to save this plan, so Terraform can't guarantee to take exactly these actions if you run "terraform apply" now.
Apply changes if the resources in the plan looks fine to you:
terraform apply
The output should look something like this:
...
Apply complete! Resources: 56 added, 0 changed, 0 destroyed.
Outputs:
ohlala_url = "http://ohlala20250328133845277200000011-xxxxxxx.eu-west-1.elb.amazonaws.com"
N.B.: there are more advanced usage of terraform that may better suit your needs.
Parameters
We suggest you create our own beta.auto.tfvars file and fill the required parameters.
Here is an example of what it may look like:
region = "us-east-1"
vpc_id = "vpc-05cbdfebd347a329d"
subnets = ["subnet-05c070af686daf105", "subnet-059ec56900f58b340"]
inbound_cidr = "88.170.94.38/32"
instance_type = "t3.medium"
key_name = "etienne-test"
region
Please enter the AWS region you will be using for your deployment. For the beta program, we plan on only releasing our AMI in us-east-1 and eu-west-1.
vpc_id
The VPC identifier of your choice.
subnets
A list of two subnets.
inbound_cidr
Enter the CIDR allowed to connect to the public ALB of Ohlala Operations for Amazon EC2. Please be vigilant and enter a limited range.
We suggest having a look at your public IP address on https://api.ipify.org.
The default mask for one IP address is /32.
instance_type
Select an instance type. For small to medium size (i.e. most deployment), t3.medium is recommended.
key_name
Please provide an existing EC2 key pair name.
Outputs
The terraform stack outputs the URL of the load balancer. Go ahead an open this link in a new tab (please allow a few minutes for the web interface to start up).
Apply complete! Resources: 56 added, 0 changed, 0 destroyed.
Outputs:
ohlala_url = "http://ohlala20250328133845277200000011-xxxxxxx.eu-west-1.elb.amazonaws.com"
✨ Ohlala Operations - Automate Windows Server Management on AWS! ✨






